 Solflare Wallet Warning Fix Guide
Solflare Wallet Warning Fix Guide
 Solflare Wallet Warning Fix Guide
Solflare Wallet Warning Fix Guide
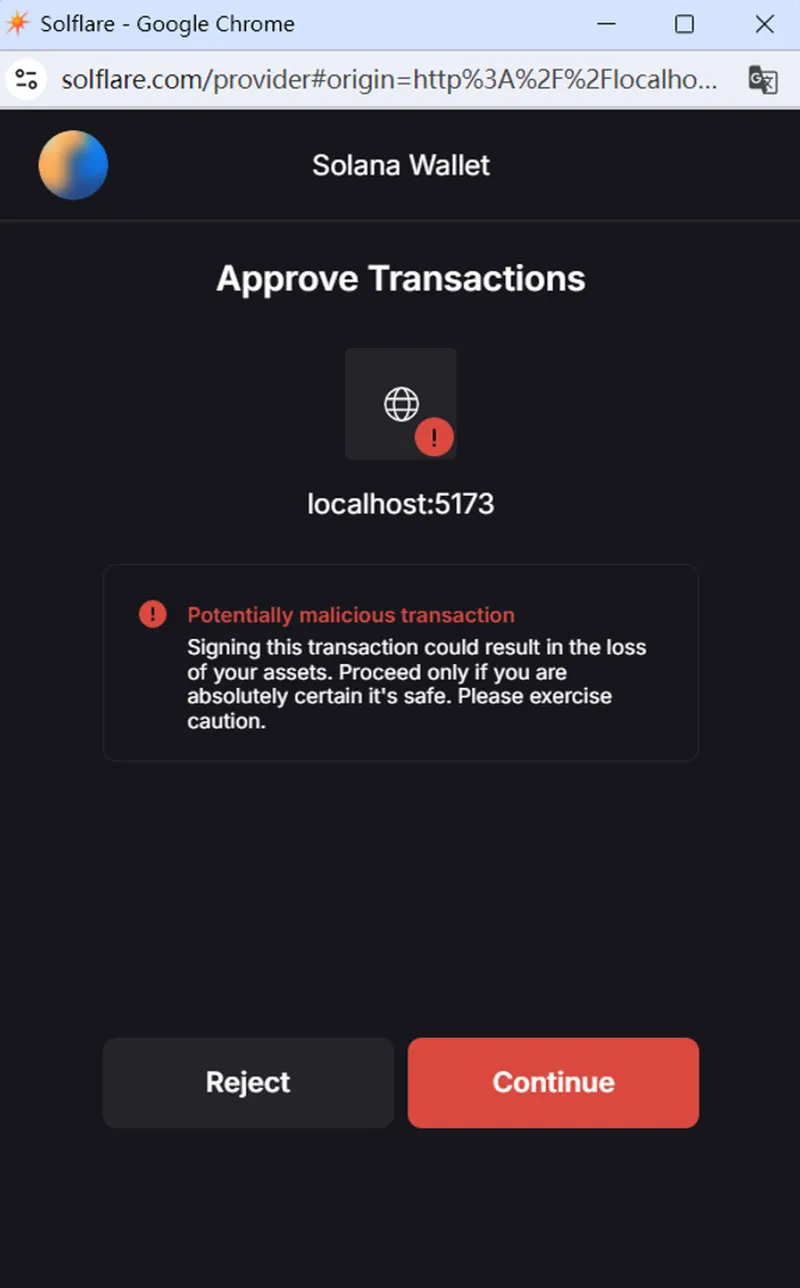
Solflare's "Potentially malicious transaction" warning is particularly impactful in the Solana ecosystem where Solflare is one of the primary wallets. This warning completely blocks transaction execution.
As a Solana-native wallet, Solflare has deep integration with Solana's security features and maintains its own database of malicious programs and addresses specific to the Solana blockchain.
Upgradeable programs without proper authority controls get flagged
Solflare and Phantom share some security data in the Solana ecosystem
Complex transactions with many instructions trigger extra scrutiny
Recently deployed Solana programs face automatic suspicion
Unusual token account creation patterns raise red flags
Consider making your program immutable or using multi-sig authority
Break complex transactions into smaller, clearer operations
Reach out through Discord or support channels with program details
Solana-specific audits from firms like Kudelski or Halborn carry weight
While they maintain separate systems, both wallets reference common Solana security resources, so flags often appear on both simultaneously.
Solflare is cautious about upgradeable programs since malicious upgrades are a common attack vector on Solana.
Not necessarily. Most wallet warnings are false positives caused by overly aggressive automated detection systems. However, it's always good practice to run a security audit to ensure your site hasn't been compromised.
Studies show that security warnings reduce conversion rates by 85-95%. For a typical DeFi project, this can mean thousands of dollars in lost revenue per day. The sooner you resolve the warning, the less impact on your business.
This is not recommended. Users have been trained to trust wallet security warnings, and asking them to bypass these protections will damage your credibility and could be seen as a red flag itself.